AD NTLM Authentication
Aside from Kerberos and LDAP, Active Directory uses several other authentication methods which can be used (and abused) by applications and services in AD. These include LM, NTLM, NTLMv1, and NTLMv2. LM and NTLM here are the hash names, and NTLMv1 and NTLMv2 are authentication protocols that utilize the LM or NT hash.
Hash Protocol Comparison
| Hash/Protocol | Cryptographic technique | Mutual Authentication | Message Type | Trusted Third Party |
|---|---|---|---|---|
NTLM | Symmetric key cryptography | No | Random number | Domain Controller |
NTLMv1 | Symmetric key cryptography | No | MD4 hash, random number | Domain Controller |
NTLMv2 | Symmetric key cryptography | No | MD4 hash, random number | Domain Controller |
Kerberos | Symmetric key cryptography & asymmetric cryptography | Yes | Encrypted ticket using DES, MD5 | Domain Controller/Key Distribution Center (KDC) |
LM
LAN Manager (LM or LANMAN) hashes are the oldest password storage mechanism used by the Windows operating system.
If in use, they are stored in the SAM database on a Windows host and the NTDS.DIT database on a Domain Controller.
Due to significant security weaknesses in the hashing algorithm used for LM hashes, it has been turned off by default since Windows Vista/Server 2008. However, it is still common to encounter, especially in large environments where older systems are still used.
- Passwords using LM are limited to a maximum of
14characters. - Passwords are not case sensitive and are converted to uppercase before generating the hashed value, limiting the keyspace to a total of 69 characters making it relatively easy to crack these hashes using a tool such as Hashcat.
- LM hash is derived as follow:
- Before hashing, a 14 character password is first split into two seven-character chunks.
- If the password is less than fourteen characters, it will be padded with NULL characters to reach the correct value.
- Two DES keys are created from each chunk. These chunks are then encrypted using the string
KGS!@#$%, creating two 8-byte ciphertext values. - These two values are then concatenated together, resulting in an LM hash.
This hashing algorithm means that an attacker only needs to brute force seven characters twice instead of the entire fourteen characters.
The use of LM hashes can be disallowed using Group Policy. An LM hash takes the form of 299bd128c1101fd6.
Note: Windows operating systems prior to Windows Vista and Windows Server 2008 (Windows NT4, Windows 2000, Windows 2003, Windows XP) stored both the LM hash and the NTLM hash of a user’s password by default.
NTHash (NTLM)
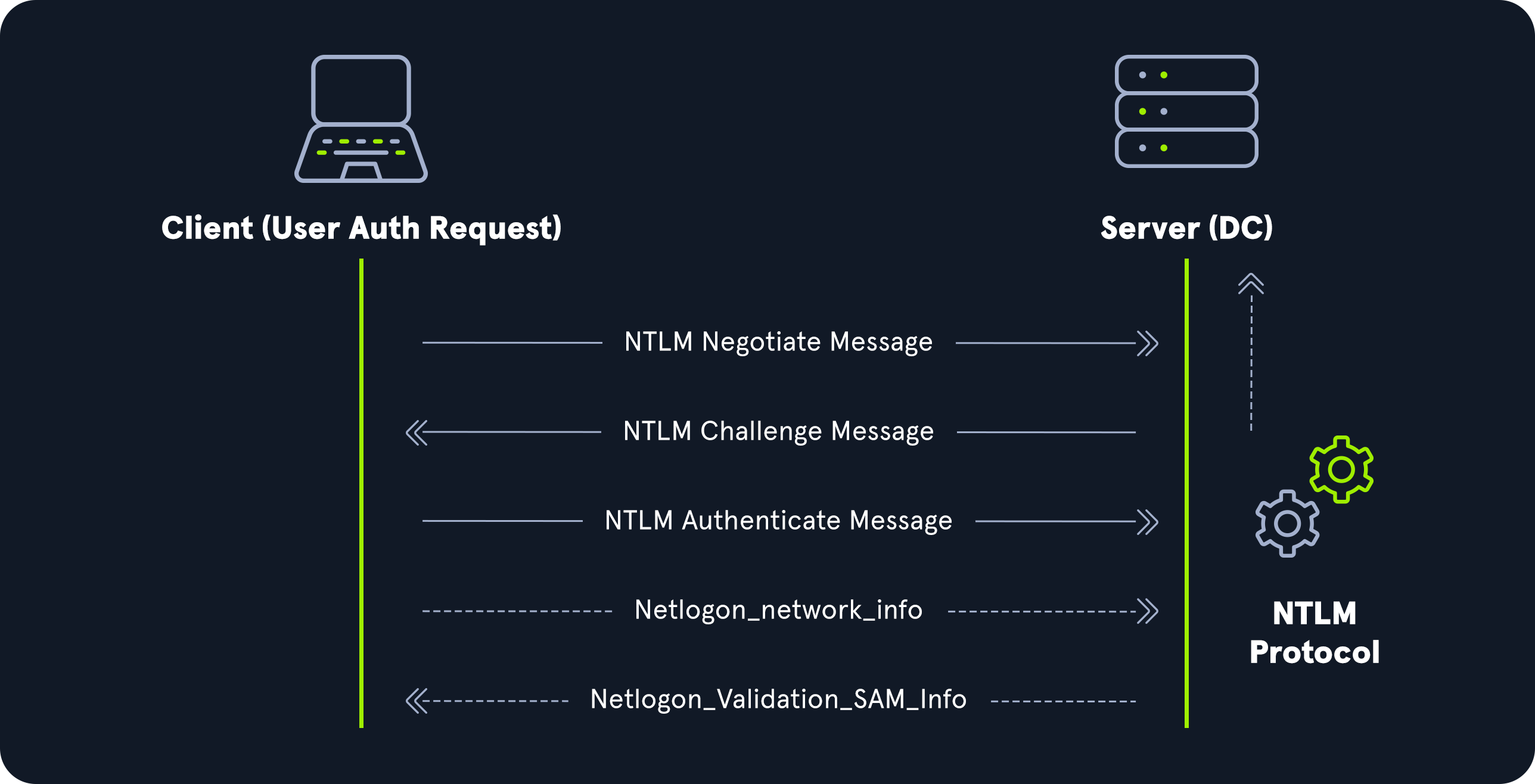
NT LAN Manager (NTLM) hashes are used on modern Windows systems. It is a challenge-response authentication protocol and uses three messages to authenticate:
- a client first sends a
NEGOTIATE_MESSAGEto the server - The server response is a
CHALLENGE_MESSAGEto verify the client’s identity - Lastly, the client responds with an
AUTHENTICATE_MESSAGE.
These hashes are stored locally in the SAM database or the NTDS.DIT database file on a Domain Controller.
The protocol has two hashed password values to choose from to perform authentication:
- the LM hash (as discussed above)
- the NT hash, which is the MD4 hash of the little-endian UTF-16 value of the password. The algorithm can be visualized as:
MD4(UTF-16-LE(password)).
NTLM Authentication Request
Even though they are considerably stronger than LM hashes (supporting the entire Unicode character set of 65,536 characters), they can still be brute-forced offline relatively quickly using a tool such as Hashcat.
NTLM is also vulnerable to the pass-the-hash attack, which means an attacker can use just the NTLM hash (after obtaining via another successful attack) to authenticate to target systems where the user is a local admin without needing to know the cleartext value of the password.
An NT hash takes the form of b4b9b02e6f09a9bd760f388b67351e2b, which is the second half of the full NTLM hash.
An NTLM hash looks like this:
1
Rachel:500:aad3c435b514a4eeaad3b935b51304fe:e46b9e548fa0d122de7f59fb6d48eaa2:::
Looking at the hash above, we can break the NTLM hash down into its individual parts:
Rachelis the username500is the Relative Identifier (RID). 500 is the known RID for theadministratoraccountaad3c435b514a4eeaad3b935b51304feis the LM hash and, if LM hashes are disabled on the system, can not be used for anythinge46b9e548fa0d122de7f59fb6d48eaa2is the NT hash. This hash can either be cracked offline to reveal the cleartext value (depending on the length/strength of the password) or used for a pass-the-hash attack.
Below is an example of a successful pass-the-hash attack using the CrackMapExec tool:
1
2
3
$ crackmapexec smb 10.129.41.19 -u rachel -H e46b9e548fa0d122de7f59fb6d48eaa2
SMB 10.129.43.9 445 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.43.9 445 DC01 [+] INLANEFREIGHT.LOCAL\rachel:e46b9e548fa0d122de7f59fb6d48eaa2 (Pwn3d!)
Note: Neither LANMAN nor NTLM uses a salt.
NTLMv1 (Net-NTLMv1)
The NTLM protocol performs a challenge/response between a server and client using the NT hash. NTLMv1 uses both the NT and the LM hash, which can make it easier to “crack” offline after capturing a hash using a tool such as Responder or via an NTLM relay attack.
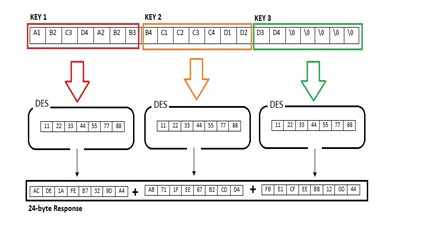
NTLMv1 challenge/response algoritm:
- the server sends the client an 8-byte random number (challenge)
- the client returns a 24-byte response.
These hashes can NOT be used for pass-the-hash attacks.
The algorithm looks as follows:
V1 Challenge & Response Algorithm
1
2
3
C = 8-byte server challenge, random
K1 | K2 | K3 = LM/NT-hash | 5-bytes-0
response = DES(K1,C) | DES(K2,C) | DES(K3,C)
In the NTLMv1 challenge/response algorithm, K1, K2, and K3 represent parts of the key used for encryption where:
- K1, K2, and K3 are derived from a combination of the LM/NT hash padded with 5 bytes of zeros
- These keys are then used with DES encryption to generate the response by encrypting the challenge (C) three times - once with each key
NTLMv1 Hash Example
1
2
u4-netntlm::kNS:338d08f8e26de93300000000000000000000000000000000:9526fb8c23a90751cdd619b6cea564742e1e4bf33006ba41:cb8086049ec4736c
NTLMv1 Is susceptible to cracking and other attacks.
NTLMv2 (Net-NTLMv2)
The NTLMv2 protocol was first introduced in Windows NT 4.0 SP4 and was created as a stronger alternative to NTLMv1.
It has been the default in Windows since Server 2000. It is hardened against certain spoofing attacks that NTLMv1 is susceptible to.
NTLMv2 challenge/response algoritm:
- Server send a 8-byte challenge to client
- NTLMv2 client sends two responses:
- first response:
- a 16-byte HMAC-MD5 hash of the challenge
- a randomly generated challenge from the client
- an HMAC-MD5 hash of the user’s credentials
- A second response is sent using:
- a variable-length client challenge including the current time
- an 8-byte random value
- the domain name
- first response:
V2 Challenge & Response Algorithm
1
2
3
4
5
6
7
SC = 8-byte server challenge, random
CC = 8-byte client challenge, random
CC* = (X, time, CC2, domain name)
v2-Hash = HMAC-MD5(NT-Hash, user name, domain name)
LMv2 = HMAC-MD5(v2-Hash, SC, CC)
NTv2 = HMAC-MD5(v2-Hash, SC, CC*)
response = LMv2 | CC | NTv2 | CC*
NTLMv2 Hash Example
1
2
admin::N46iSNekpT:08ca45b7d7ea58ee:88dcbe4446168966a153a0064958dac6:5c7830315c7830310000000000000b45c67103d07d7b95acd12ffa11230e0000000052920b85f78d013c31cdb3b92f5d765c783030
We can see that developers improved upon v1 by making NTLMv2 harder to crack and giving it a more robust algorithm made up of multiple stages.
Domain Cached Credentials (MSCache2)
In an AD environment, the authentication methods mentioned in this section and the previous require the host we are trying to access to communicate with the “brains” of the network, the Domain Controller.
Microsoft developed the MS Cache v1 and v2 algorithm (also known as Domain Cached Credentials (DCC) to solve the potential issue of a domain-joined host being unable to communicate with a domain controller (i.e., due to a network outage or other technical issue) and, hence, NTLM/Kerberos authentication not working to access the host in question.
Hosts save the last ten hashes for any domain users that successfully log into the machine in the HKEY_LOCAL_MACHINE\SECURITY\Cache registry key.
!!! These hashes cannot be used in pass-the-hash attacks. Furthermore, the hash is very slow to crack with a tool such as Hashcat, even when using an extremely powerful GPU cracking rig, so attempts to crack these hashes typically need to be extremely targeted or rely on a very weak password in use. !!!
These hashes can be obtained by an attacker or pentester after gaining local admin access to a host and have the following format: $DCC2$10240#bjones#e4e938d12fe5974dc42a90120bd9c90f.
It is vital as penetration testers that we understand the varying types of hashes that we may encounter while assessing an AD environment, their strengths, weaknesses, how they can be abused (cracking to cleartext, pass-the-hash, or relayed), and when an attack may be futile (i.e., spending days attempting to crack a set of Domain Cached Credentials).