Active Directory
active directory concepts and main attack paths
AD is based on the protocols x.500 and LDAP that came before it and still utilizes these protocols in some form today. AD provides authentication, accounting, and authorization functions within a Windows enterprise environment
It is designed to be backward-compatible, and many features are arguably not “secure by default,” and it can be easily misconfigured. This weakness can be leveraged to move laterally and vertically within a network and gain unauthorized access. AD is essentially a sizeable read-only database accessible to all users within the domain, regardless of their privilege level
Table of Contents
Fundamentals:
Protocols:
Methodology:
Tools
Main Attack Path
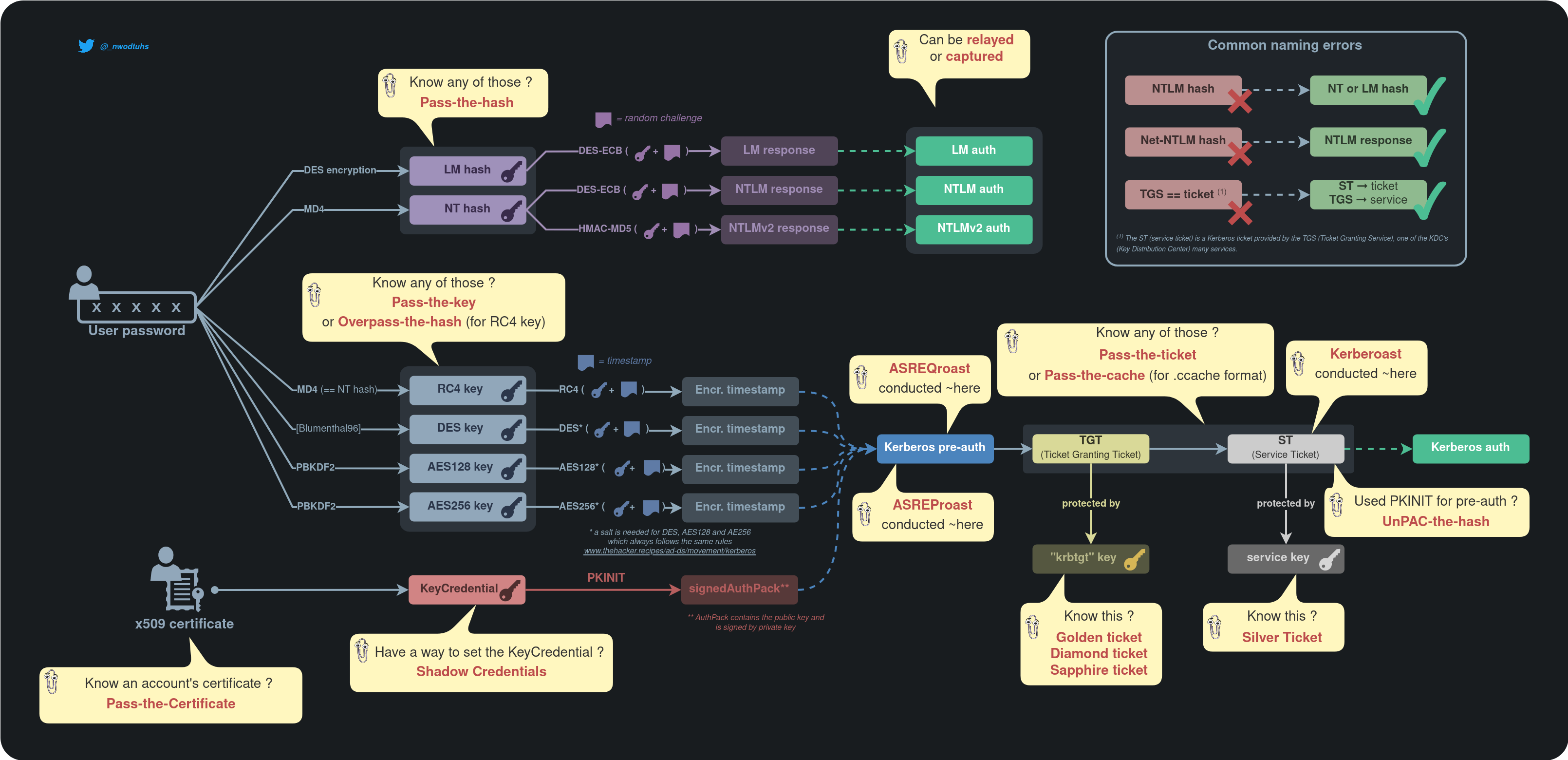
Typology of keys are defined in Kerberos section
- Target: Users/Service/Security Principal account with human defined password
- Require: an User access to AD
- Scope: Collecting ST and cracking weak service key to retrieve credentials ?
- Target: Users/Service/Security Principal with Kerberos preauthentication disabled
- Require: an User access to AD
- Scope: Collecting TGT and cracking weak user session key to retrieve credentials ?
- Target: Users/Service/Security Principal
- Require: access to AD infrastructure, Knowledge of the user key or user password
- Scope: Impersonating target/gaining TGT of the user to access different services
- Target: Domain Controller
- Require: Domain admin privileges (
DS-Replication-Get-ChangesandDS-Replication-Get-Changes-Allspecifically) - Scope: retrieve Domain Controller data simulating a DCSync, data obtained typlically are
- LM and NT password hashes
- Passwords stored using reversible encryption
- Kerberos keys (DES, AES128 and AES256)
- Domain controller’s SAM secrets
- Domain controller’s LSA secrets
- Target: KDC
- Require: Domain admin privileges or krbtgt key
- Scope: Forge a TGT with a PAC, used for lateral movement
- Target: Service
- Require: service key
- Scope: Forge a ST with a PAC to access target service
- Target: GPOs
- Require:
WritePropertyto theGPC-File-Sys-Pathproperty of a GPO (specific GUID specified)GenericAll,GenericWrite,WritePropertyto any property (no GUID specified)WriteDacl,WriteOwner
- Scope: Perform malicious actions editing existing GPOs
[TODO]
https://www.thehacker.recipes/ad/movement/trusts/
https://www.thehacker.recipes/ad/movement/kerberos/delegations/unconstrained
https://www.thehacker.recipes/ad/movement/kerberos/delegations/constrained
[Useful resource]
https://github.com/Orange-Cyberdefense/ocd-mindmaps
https://github.com/S1ckB0y1337/Active-Directory-Exploitation-Cheat-Sheet